Hacking the White House: Election Fraud in the Digital Age
Hacking the White House: Election Fraud in the Digital Age
Abstract
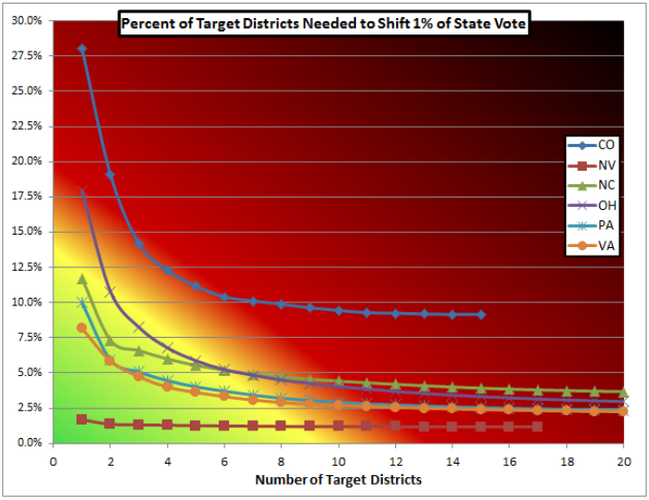
Our founding fathers fought a war to remove the shackles of colonial tyranny and install a democracy guided by the principle of ‘‘one man one vote.’’ The modern American electorate, however, is losing confidence in the integrity of its voting system. At the same time, computer security researchers have revealed that many of today’s voting machines are highly flawed and vulnerable to cyber‐attack. Together this begs the question: are American elections safe from attack? This thesis is an exploration of not only how credible the threat of a stolen election is given the voting systems operating today, but also in what ways a theoretical attack might take place and what protective measures can be implemented to prevent an attack. This thesis first examines why these vulnerabilities exist by exploring the history of voting machines and revealing that the persistence of these flaws is caused by repeated shifts in the relative importance of privacy, usability, transparency and cost. It then explores what types of attacks can occur by focusing on both attacks against the system in which the machines operate, and those against the machines themselves. This reveals that scalability, ease of access, and likelihood of detection determine the profitability of each attack. Where, when and how an attack against the voting system will occur is explored next by simulating a theoretical attack against the 2012 election. Finally, this thesis ends with a discussion of how to safeguard the American electoral system. This thesis concludes that: paper trails and audits are effective measures to radically increase the difficulty of attack, future systems need to be designed to balance privacy, usability, transparency and cost, voter education is a vital part of any security strategy, and safeguards against insider influence on the voting process can greatly hinder the scalability of an attack. Elections can be made quite secure if these conclusions are considered, followed and implemented.